OAuth Management
OAuth is a protocol that allows a user to grant a third-party application access to their protected resources, without revealing their credentials or identity.
To use the oAuth structure in your application:
You should reach out to the Plateau Security team at PlateauSecurity@softtech.com.tr
- In Plateau Studio, navigate to the Explorer tab and go to Application Settings and locate the OAuth screen.
- Enter the OAuth definitions provided by the Plateau Security team.
Keycloak("^20.0.3") is used in the oAuth protocol infrastructure.
Advanced Protocol Settings
In this section, you'll find detailed instructions on filling out the fields for the Advanced Protocol Settings. These settings are essential for configuring OAuth in your application, ensuring secure and seamless integration with third-party services.
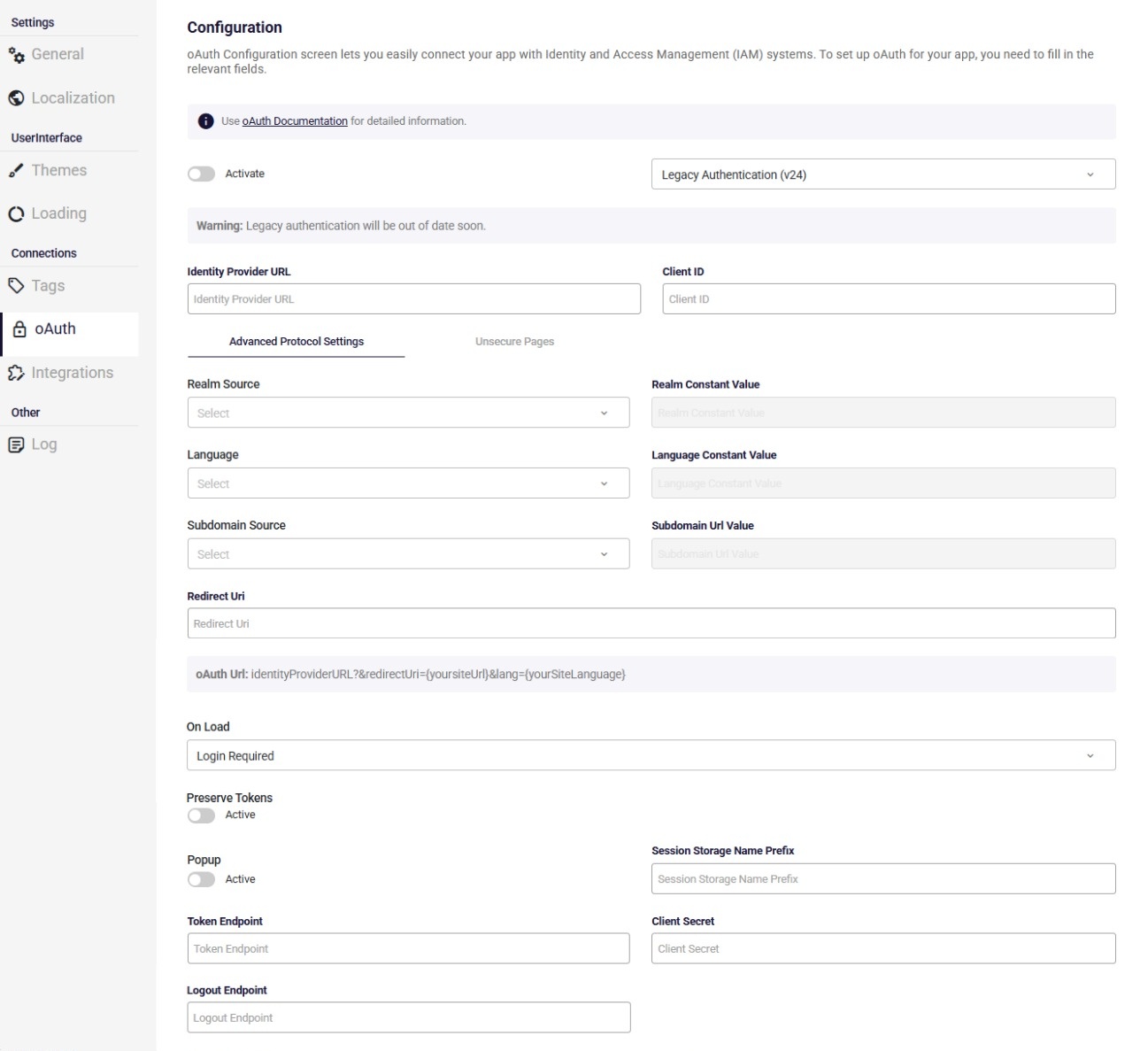
- Authentication Version: Specifies which version of Keycloak is used for handling OAuth authentication.
Default is v24. Choose v26 if your application is configured to use the newer Keycloak version.
- Legacy Authentication (v24): Uses the established Keycloak v24 flow, compatible with existing configurations and behaviors.
- New Authentication (v26): Enables the updated Keycloak v26 flow, which introduces improvements in security, token handling, and compatibility with modern OAuth standards.
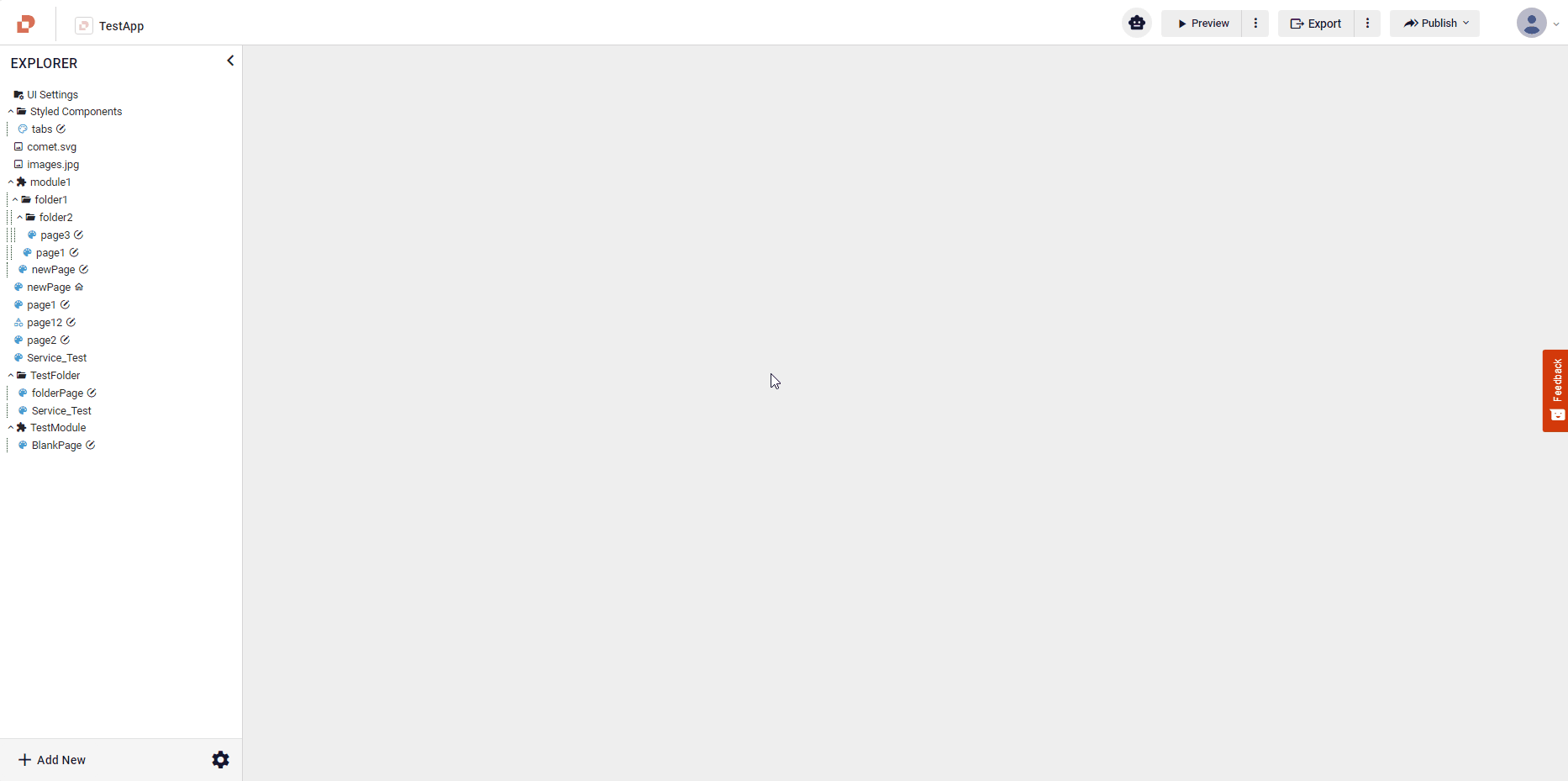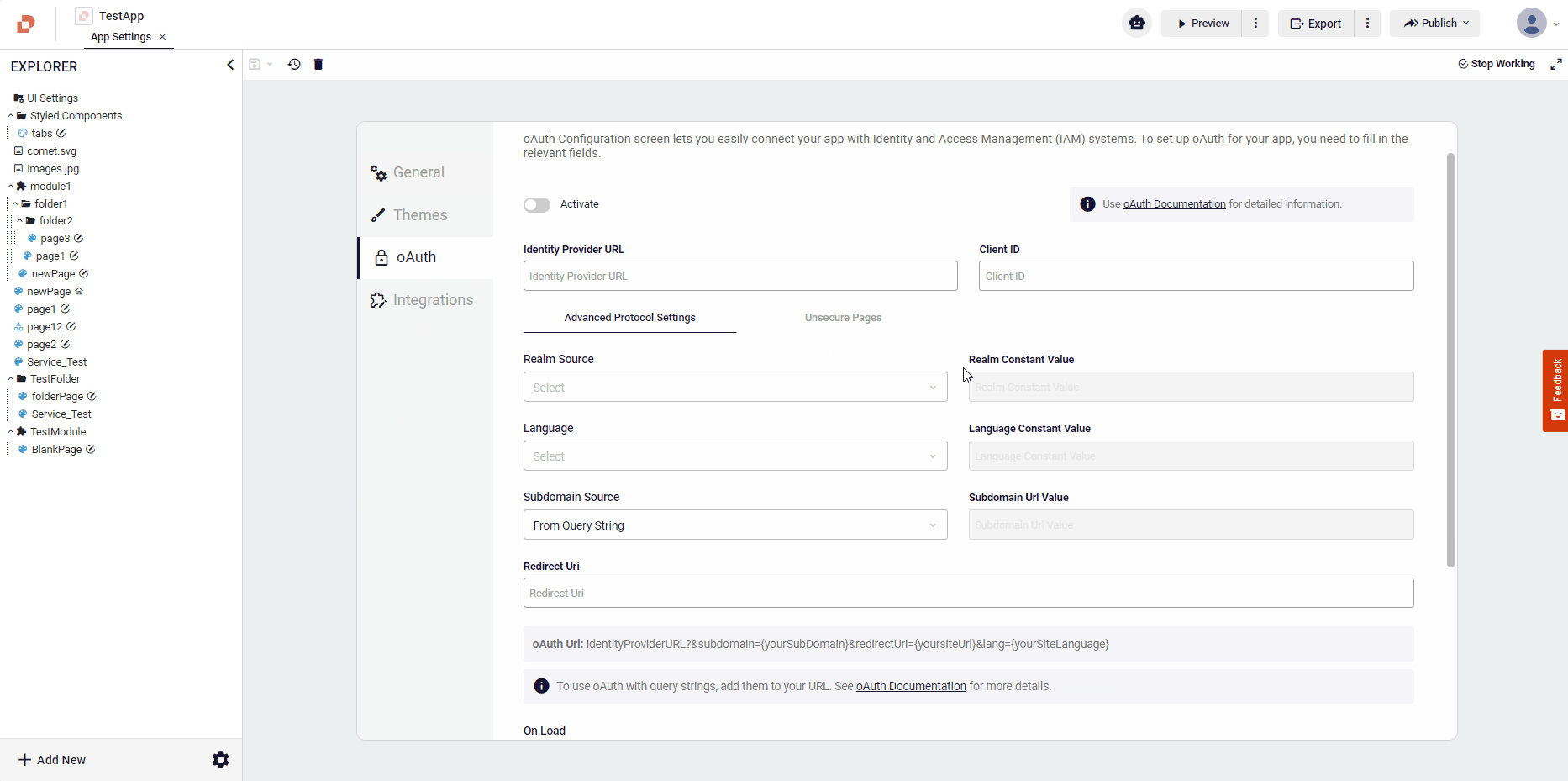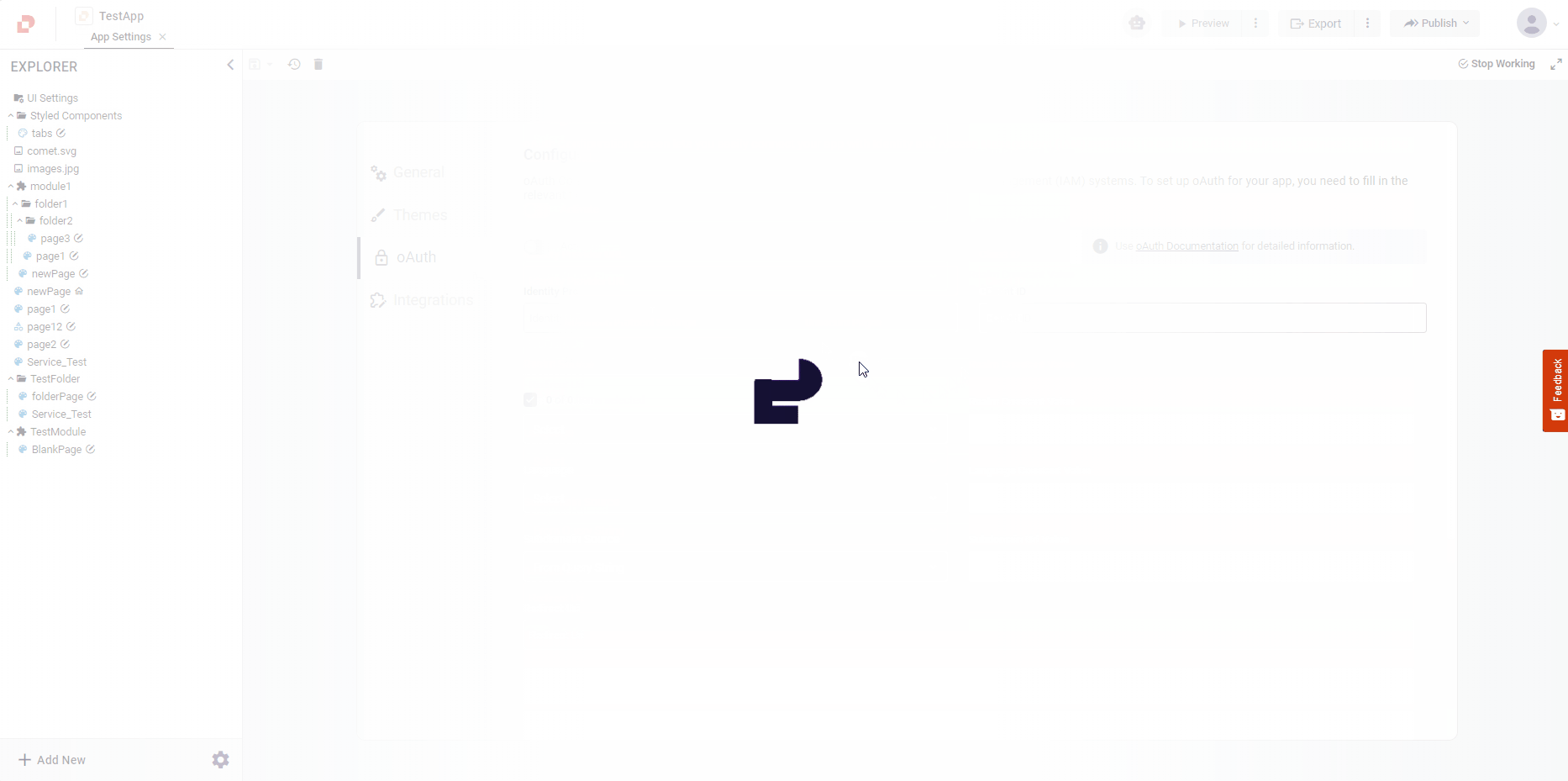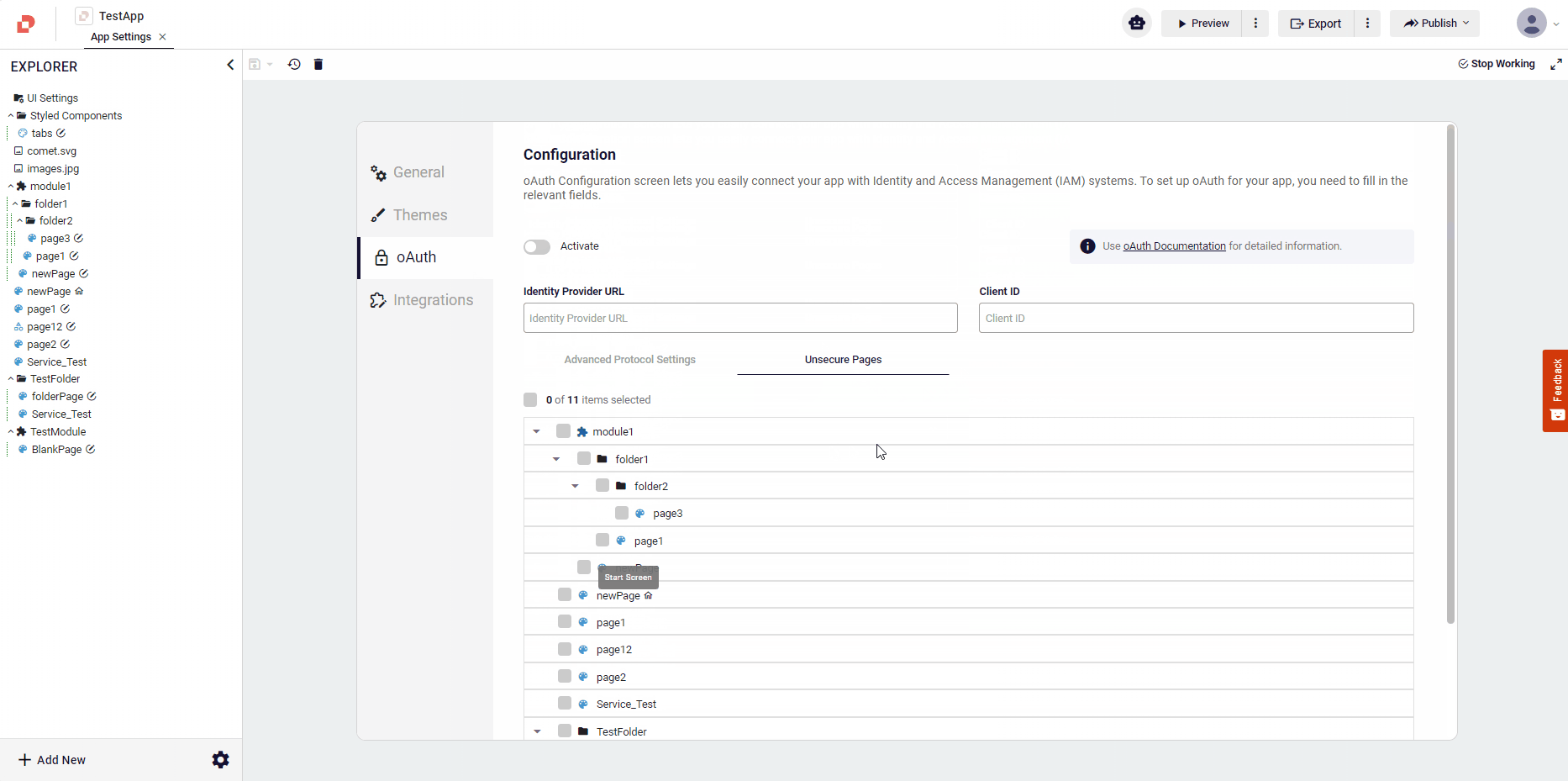
- Identity Provider Url: This is the URL of the authorization server that issues access tokens and authenticates the user. You need to enter a valid URL that supports the OAuth protocol.
For Example: https://accounts.google.com
Client ID: This is the identifier of the client application that requests access to the user’s resources. It is assigned by the authorization server when the client registers with it. You need to enter the ClientID that matches your application.
Realm Source: This is an optional parameter that specifies the scope of protection in the authentication exchange. It is used to partition the credential space of different protection domains. You can choose to enter a constant value or read it from the query string of the user site URL.
For Example: photos.example.com
Language: This is an optional parameter that specifies the language for the authentication interface. It is used to set the language in which the authentication prompts and messages will be displayed to the user. This is particularly useful for applications that support multiple languages and need to provide a localized user experience. You can choose to enter a constant value or read it from the query string of the user site URL.
Subdomain Source: This is an optional parameter that specifies the subdomain of the client application that requests access to the user’s resources. It is used to differentiate between multiple instances of the same application hosted on different subdomains. You can choose to enter a constant value, read it from the query string, or read it from the subdomain of the user site URL.
For Example: dev.yoursite.com
- Redirect Uri: This is the URL that the user will be redirected to after the authorization is completed. It must match the registered redirect URI of your application.
For Example: https://yoursite.com/callback
On Load: This is a parameter that specifies the authentication method. Utilize the login function to enable automatic authentication by passing either login-required or check-sso to the init() function. The login-required option prompts for login if the user is not authenticated, while check-sso only authenticates if the user is already logged in.
Preserve Tokens: This is a switch that determines whether the access token will be preserved in the session or not. If enabled, the access token will be stored in the session and can be reused for subsequent requests. If disabled, the access token will be discarded after each request and a new one will be obtained.
Popup: This is an optional switch that determines whether a new IAM login is initiated in a popup window or not. If enabled, the popup appears, allowing you to trigger a new IAM login with updated settings within the same application or page. If disabled, the popup does not appear, and attempting a second IAM login won’t work due to an existing active login session.
Session Storage Name Prefix: This is an optional input that contains a token’s prefix, which is created by the second IAM login using a popup. By using this prefix, session storage can manage and differentiate between tokens generated by different IAM logins.
Token Endpoint: This is the URL of the authorization server where the client application exchanges the authorization code for an access token. The token endpoint is a crucial part of the OAuth flow, enabling the client to obtain the access token needed to access protected resources.
For Example https://oauth2.googleapis.com/token
Client Secret: This is a confidential string assigned to the client application by the authorization server. It is used to authenticate the client application when requesting access tokens. The client secret must be kept secure and should not be shared or exposed in client-side code.
Logout Endpoint : This is used to log users out of an application and invalidate their session. This is typically done by calling a specific URL endpoint provided by the Identity and Access Management (IAM) service.
Unsecure Pages
The Unsecure Pages specify the list of pages that will be opened before authentication. These pages are not protected by OAuth and can be accessed by anyone without authorization. You can select multiple pages from the list that you'd like to make unsecure.
For Example: home, about, contact.